
Golang language
1. Simplicity: The language is designed to be simple and easy to read, with a clean syntax and minim...


1. Simplicity: The language is designed to be simple and easy to read, with a clean syntax and minim...
you need learn about the circuit board (PCB) in electronic field and then you need learn about elect...
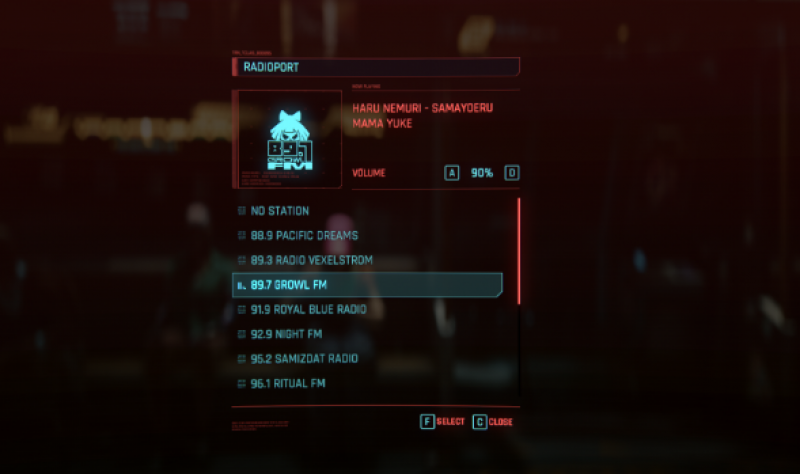
FM radio hacking works by exploiting the principles of frequency modulation to intercept, modify, or...

FM radio hacking holds considerable significance for a range of reasons across educational, technolo...

Attackers can exploit radio signals and mobile phones to steal protected data through several sophis...

FM radio hacking typically refers to various activities involving the manipulation, modification, or...

What is Linux?
Just like Windows, iOS, and Mac OS, Linux is an operating system. In fact, one...

In Israel, programming languages and technologies developed for military use have played a significa...

In the previous section, we mentioned that most computers rely on a CPU, and a CPU can understand a ...

here are some of them:
1. Fortran (1957) - Developed by IBM, Fortran is one of the oldest hi...

Mainly there are five types of programming languages, they are:
1) Procedural Programming Lan...
Programming languages are mainly differentiated into two categories: high and low. Languages are cat...

A programming language is a computer language that is used by programmers (developers) to communicat...

in September 2010 that the malware was of Israeli origin, and that it targeted Iranian nuclear facil...

1. Update your frontline defenses
Adhere to policies and best practices for application, syst...

1982
A plain and simple "unwanted software" is the most widely accepted malware d...
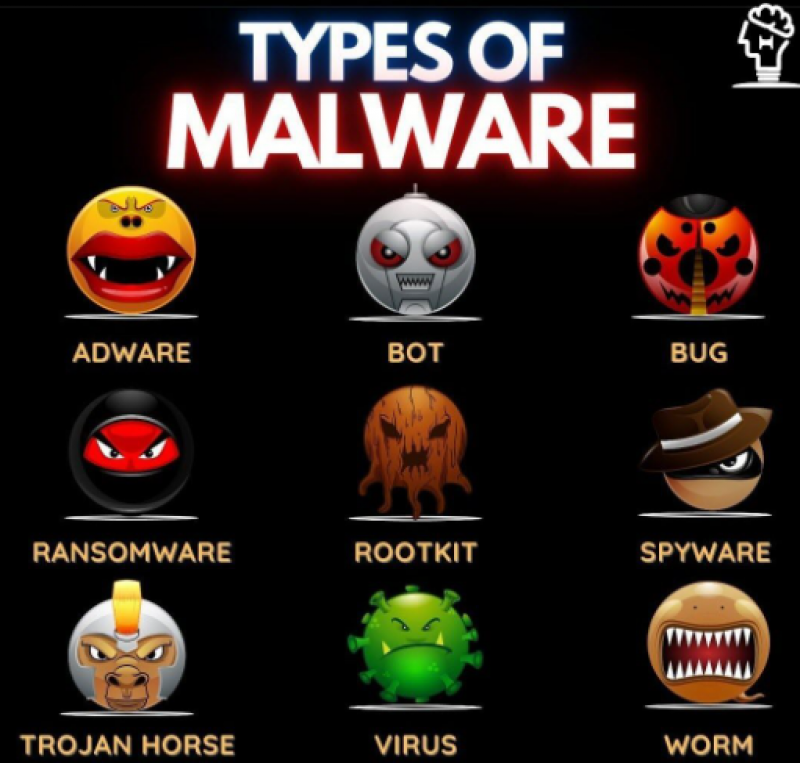
here is the most common type of the malware:
1. What are Computer Viruses?
A virus is a ty...

malware means virus, in the real world we have a virus biologically such COVID 19 or corona and so o...

Cyberwars Begin
The Baltic nation of Estonia was the first state hit by a massive cyberattack...

The Israeli cyber startup scene is the second largest in the world, drawing both foreign investment ...

friend sends you the link to a National Geographic video about the Kurdish Peshmerga fighting the Is...
The United States government is taking a series of actions today against cyber actors which are conn...

Fight between USA and China that attacking each other by cyberwarfare field, and China try to steal ...

Sometimes to determine the other person's intelligence level for technology and to know his go...
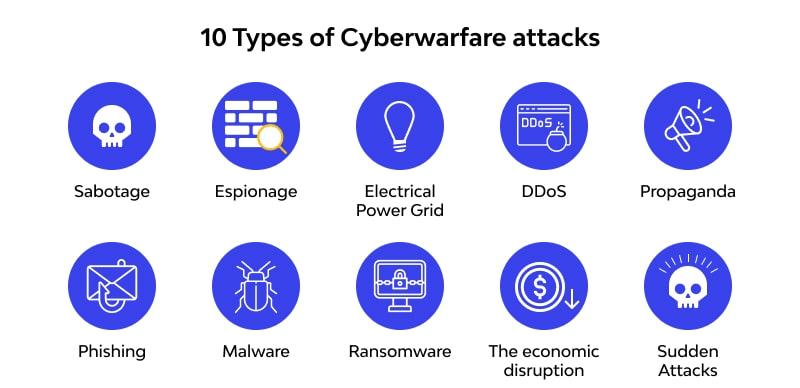
Types of Cyberwarfare
1. Espionage
- Spying: Stealing secrets or sensitive information ...

A Cyber Warfare Technician, often part of military or government cyber units, specializes in:

Israel has a biggest power in the middle east and no country can do challenge with a Israel and Isra...

Unit 8200 is indeed a key entity within the Israeli Defense Forces (IDF) responsible for signals int...

1) National Security: Protects against threats to a nation's safety and sovereignty and protec...

USA - Israel cyberwarfare Engineer attack Iran Nuclear projects...

Navy has role in protect U.S interests sea, and the Cyber warfare Engineer in NAVY army protect nava...

Cyber warfare is Cyber warfare is the use of digital attacks by one country or a person or Agency to...